Hello, World! I’m Mohe, a cybersecurity student at Lincoln University, Malaysia. I’m passionate about all things cybersecurity—from understanding network protocols to building tools that explore real-time security challenges. I’m comfortable working on both Linux and Windows systems and enjoy digging deep into how systems and networks operate. I also actively participate in CTFs to sharpen my practical security skills.
I love programming and applying my knowledge to hands-on projects. Outside of my studies, I enjoy web development with Next.js, React, and TypeScript, creating applications that are both functional and user-friendly.
Some of my notable projects include this website and Password Manager, designed for secure data handling, and a RAG App, exploring retrieval-augmented generation concepts.
I’m always curious, experimenting, and seeking ways to turn ideas into real, working solutions.
CyberSecurity & Web Development hobbyist
Malyasia, Kuala Lumpur
cybersecurity and full-stack developer who loves building secure web apps, solving CTF challenges, and sharing knowledge through blogs and projects.
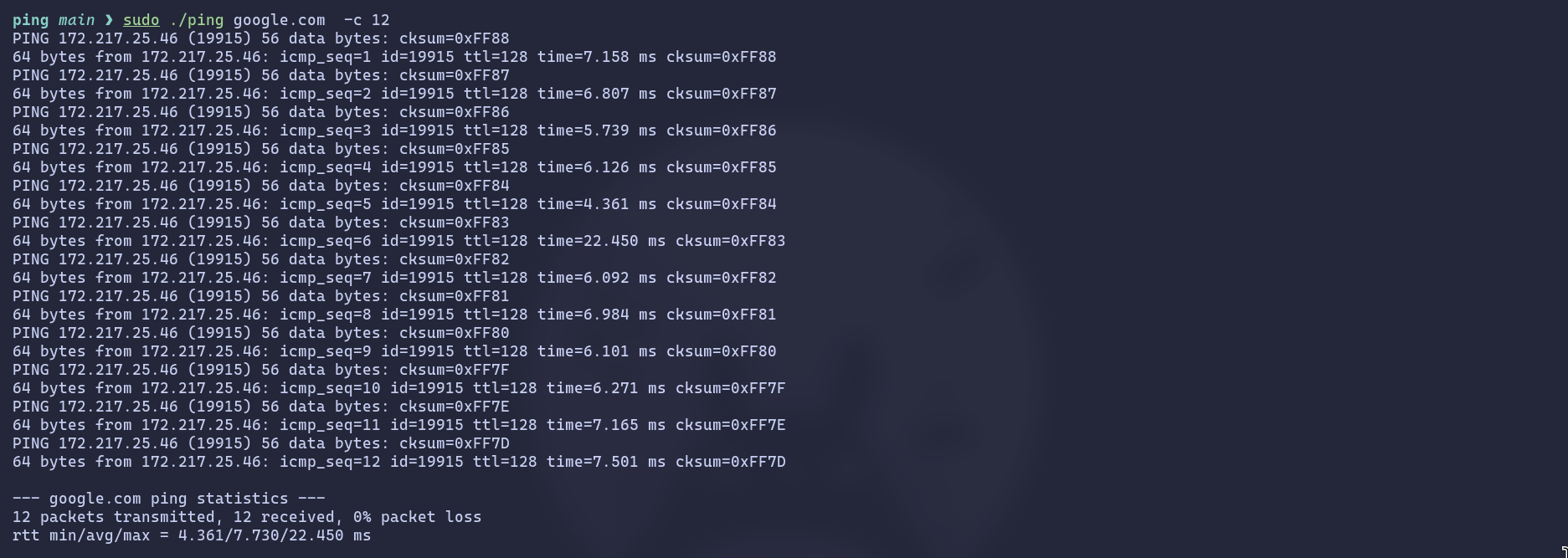
A C++ raw ICMP ping utility that sends ICMP Echo Requests to a host, measures round-trip time, and prints results. Uses threads to receive replies, calculates checksums, handles timeouts, and shows statistics including min/avg/max RTT and packet loss. Supports -c for count.
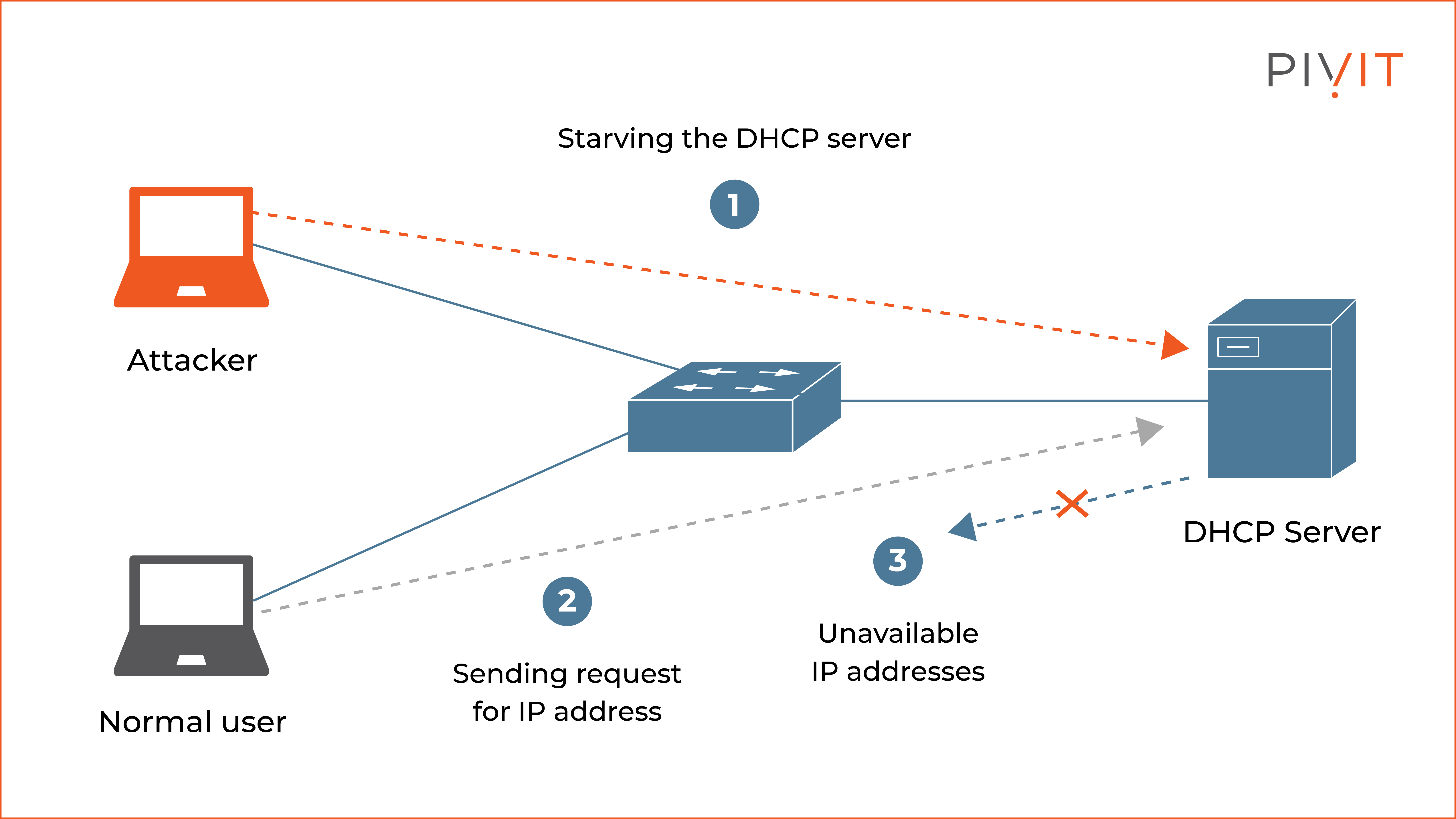

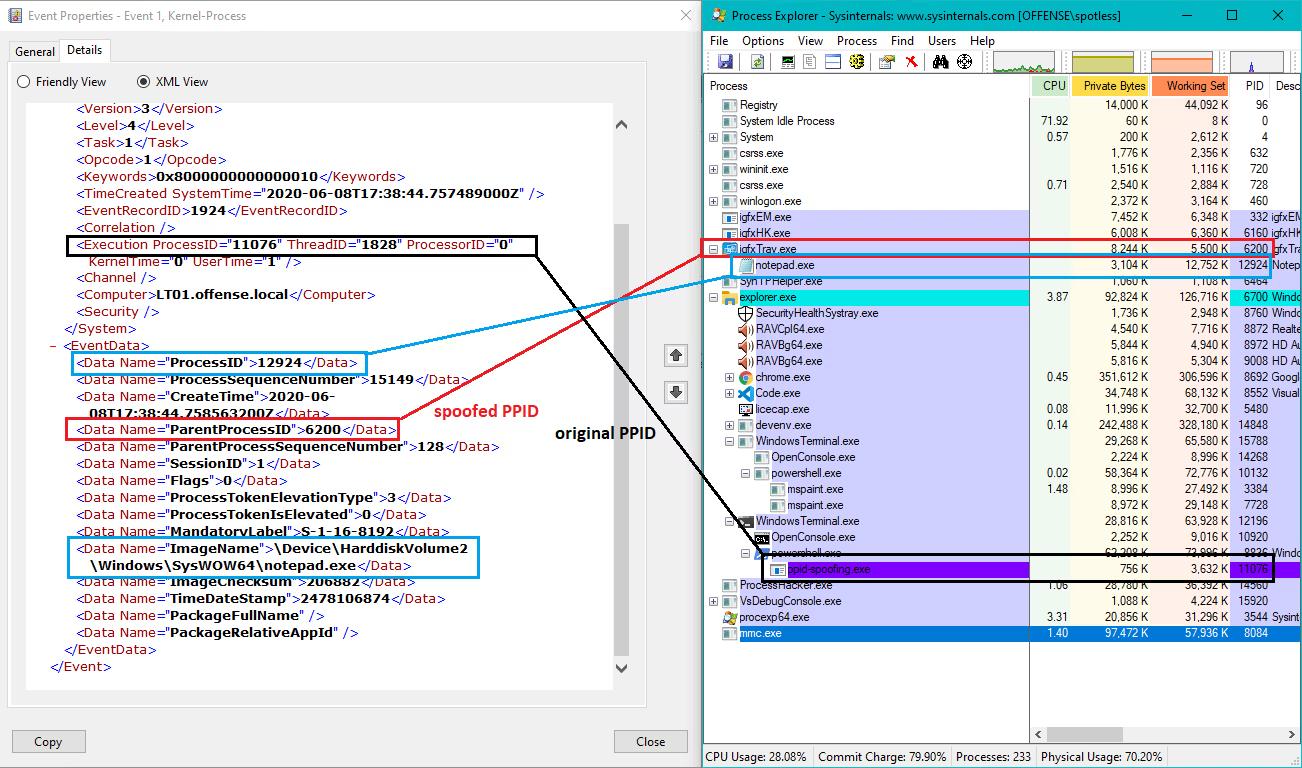
I write about cybersecurity, programming, and problem-solving from building secure full-stack applications to breaking down CTF challenges and practical guides for developers. My goal is to share insights that help others learn, build, and stay ahead in tech.
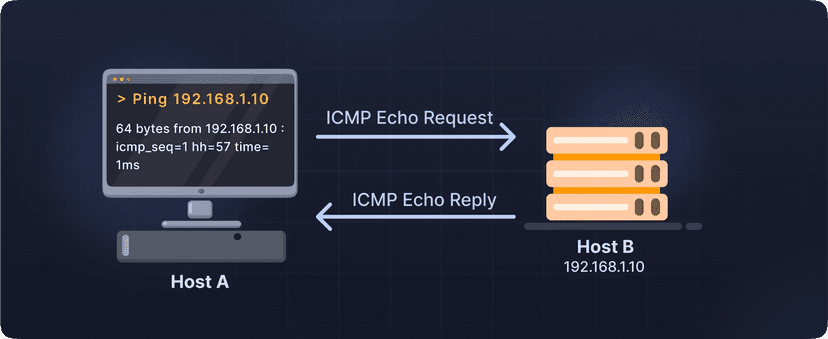
A C++ raw ICMP ping utility that sends ICMP Echo Requests to a host, measures round-trip time, and prints results. Uses threads to receive replies, calculates checksums, handles timeouts, and shows statistics including min/avg/max RTT and packet loss. Supports -c for count.

TombWatcher, a complex Active Directory machine. This walkthrough covers Kerberoasting, abusing Group Managed Service Accounts (gMSA), and escalating privileges through a creative ADCS ESC15 certificate vulnerability. A multi-stage attack from user to full domain compromise.

From a null-byte upload to SYSTEM. Pivoted through users by abusing ADCS, then leveraged SeManageVolume and SeImpersonate privileges to dump the final admin hash.

Exploited CVE-2024-53677 for access, found tomcat-users.xml with james password, then used sudo tcpdump to create SUID /tmp/bash and gained root.